What is Network Penetration Testing?
As the global online presence increases in intensity and quality, the number of associated cyber threats also increases in tandem. We are required to constantly supervise network security, web applications, devices, servers, etc, and find better ways to do the same, adapting to more and more dangerous online security issues.
This is where network penetration testing steps in to help you find out such cybersecurity issues before they negatively impact your system, through the process of ‘ethical hacking’ and simulated threats.
In this context, network penetration testing (or, pen-test for short) is a tool of great importance, useful in detecting security misconfigurations and possible exposure of vulnerabilities and threats that can harm any organization’s = networks, websites servers, and other applications when exploited by the hackers.
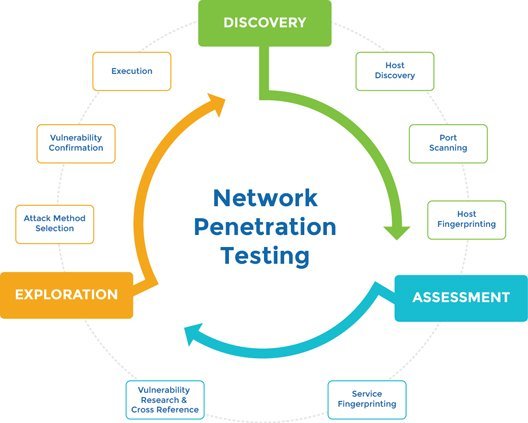
For easier reference, imagine it to be a mock drill against known cyber threats. So, as to identify any security issues as they occur or after, to be worked on later for better strengthening. It is important to realize that an alternate scenario leaves systems unprotected and data ripe for picking by unlawful hands, making network pen testing a necessity.
Sometimes, companies who have put their systems through vulnerability scanning doubt the relevance of pen tests since both processes have the same goal. However, pentests often (and must) happen after vulnerability assessments. While the latter uses automated website scanners to conduct security checks, the former puts forward stimulated cyber attacks. If both point out the issues in the firewall and other security measures, network pen tests bring in more concerted efforts to recognize the problem and solve it. Using high-quality versions of both allows one to cyclically go through a website vulnerability scanner, attain risk reports and the varying levels of danger, then use this information to conduct a pen test before preparing the final assessment and applying fixes.
Why do you need Network Penetration Testing?
1. Protect your data
Single-handedly the most important reason, every organization must guard itself against data breaches. Pen testing networks often function like ethical hacks and simulate cyber attacks as best as possible. A small weakness has the potential to let out sensitive information, affecting your customers’ trust and the more serious violation of various rules and regulations. Here, a helpful way to determine the level of possible intrusion is to identify the different levels of risk that you are exposed to.
2. Ensuring overall security
Be it the structure of your business as a whole, sensitive data, or newly released applications, ensure that no overlooked flaw can compromise your integrity through network pentest. Security assessments and website security scans should be a part and parcel of any new initiatives, especially if there is the management of important data. Some examples of such flaws include SQL injections, weakly configured firewalls, outdated software, and traditional virus or malware.
3. Compliance requirements
Certain regulations insist on penetration testing services, no matter the industry. For example, data security for the payment card industry ensures such tests for the protection of customers’ sensitive information (PCI DSS).
4. Continued maintenance
Network pen tests require multiple runs through a continuous time period to ensure long-term security. Professionals hired for this purpose will also look over the security controls used for the business network such as firewall, layered security, encryption processes, etc. Proper penetration tests, keeping in mind the needs of the system, client, and overall security.
Comments
Post a Comment